 The discovery of the Stuxnet computer worm in 2010 and the more recent spyware attack known as Flame – both of which specifically targeted the Iranian nuclear development program – has led to wild speculation by subject matter experts from almost every discipline imaginable. But the common thread that binds the analysis of these experts together has been the conclusion that the great “cyber wars” of the 21st century have begun.
The discovery of the Stuxnet computer worm in 2010 and the more recent spyware attack known as Flame – both of which specifically targeted the Iranian nuclear development program – has led to wild speculation by subject matter experts from almost every discipline imaginable. But the common thread that binds the analysis of these experts together has been the conclusion that the great “cyber wars” of the 21st century have begun. But intelligence officers see things differently. I spent seven years as a military intelligence officer before becoming a journalist. And when I look back at my days supporting senior decision makers during multiple real-world crises, from Somalia to Haiti to the war in Bosnia, I cannot help but be reminded of the deliberate nature of the intelligence cycle. From direction through collection, processing, production and dissemination – nothing is done for the sake of being able to do it. There are always strategic-level policies or tactical military objectives that dictate your actions.
And that’s exactly where the media analysis of the implications of the Stuxnet-Flame connection break down. Nobody is talking about what these two cases of highly sophisticated, state-sponsored cyberattacks really signal for the future. From an intelligence officer’s perspective, they both have far less to do with so-called “cyber war” and more to do with the increasing possibility of yet another real war in the Middle East.
Here’s why.
Discerning direction
Given the absolute necessity of preventing Iran from developing a nuclear weapon, it is completely plausible that a covert cyber operation designed to both sabotage and collect critical intelligence on the Iranian nuclear program was, in fact, initiated under the Bush administration and continued under President Obama.
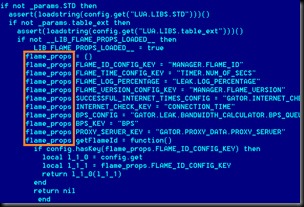
But since very few people in the US government were privy to the intelligence requirements developed based on the information needs of the president and his national security advisers, we are left to decipher what those requirements (the direction stage of the intelligence cycle) might have been. And we can do that based on what we know about the information targeted by the Flame malware. Every day we are learning more about Flame thanks to the analysis coming out of cybersecurity research firm Kaspersky Lab, the firm that discovered the attack.
As more details emerge about the code that powered this massive attack -- massive both in the size of the code (20 megabytes) and the sophistication of its targeting and collection processes -- we can begin to see potential operational links to the information being collected.
Geography/targeting
When coupled with the fact that Flame shares many characteristics with Stuxnet, (which had a much simpler offensive/destructive mission, setting back
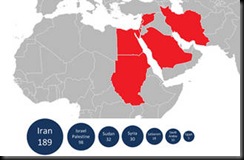 the Iranian nuclear program by at least six months), the geography and highly targeted nature of Flame continues to point to Iran’s work on a nuclear weapons program. Although Flame infections have been detected elsewhere around the world, the primary targets (more than 600 systems/networks) have been located in Iran, including many in the country’s energy/nuclear industry.
the Iranian nuclear program by at least six months), the geography and highly targeted nature of Flame continues to point to Iran’s work on a nuclear weapons program. Although Flame infections have been detected elsewhere around the world, the primary targets (more than 600 systems/networks) have been located in Iran, including many in the country’s energy/nuclear industry. Operational Implications: Highly targeted at the infrastructure serving the world’s next, most likely military hot spot. Not a coincidence.
Specificity/human interaction
One of the more unique aspects of Flame is its ability to search for specific types of information and network activity and, once found, download/activate particular modules of code designed to capture that information and communicate it back to any one of at least 80 domains hosted on a dozen command and control servers using a covert secure sockets layer (SSL) connection.
The attackers responsible for Flame also seemed to know exactly what they were interested in. For example, once Flame has infected a few dozen systems its handlers collect and analyze the information gathered. If the information on some of those computers turns out not to be of interest, they uninstall Flame using a specific removal module (named “browse32”), leaving the malware on only the high pay-off machines. Then a new round of targeting is started.
Operational Implications: Attackers have been given clear direction and know what their information requirements are to support specific intelligence requirements. And the design of the malware, coupled with no evidence of financial or black market activity, indicates they wanted the operation to go undetected as long as possible. That’s the fingerprint of a professional intelligence organization.
Specific actions need specific intelligence
As soon as Flame infects machines, it begins a series of functions to covertly steal data, including snapping screen captures and targeting email and chat sessions. And while many have tried to find unique aspects to the mechanics of how the malware is accomplishing this, the skilled intelligence officer sees something different.
AutoCAD
According to Kaspersky analysts, Flame has a particular appetite for AutoCAD engineering design files.
Operational Implications: Intelligence agencies don’t steal AutoCAD engineering documents from nuclear power plants to conduct cyber war. They steal these documents to potentially understand several things:
- At what stage is the Iranian nuclear program developmentally? Are they building new facilities? What type of facilities?
- Do we have engineering and design information about existing facilities? Do we have enough information to successfully target these facilities with kinetic weapons? How thick are the walls? What materials were used in the construction of the facility? How deep is it located underground? How big is the facility? Where are the critical components of the facility located? When attacking critical infrastructure it is not always necessary to destroy the entire facility. Targeting critical components that are difficult to replace can often do the trick, especially when your policy objective is to prevent a process from moving forward.
Flame has the ability to record ambient sounds through a computer’s integrated microphone. In addition, Flame can leverage Bluetooth devices to collect information about discoverable devices near the infected machine. It can also turn the infected machine into a beacon and make it discoverable via Bluetooth and provide general information about the malware status encoded in the device information.
While this is not a new development in the world of information warfare (every new intelligence officer in the late 1980s was briefed about the threat of the KGB and other organizations turning telephones in offices into live beacons/transmitters), it does say something about the attackers’ understanding of the challenges they faced in their collection environment.
After Stuxnet and Flame’s predecessor, Duqu, Iranian nuclear scientists and officials were likely pushed into modes of communication thought to be more secure than email. They likely began holding more in-person meetings to discuss nuclear development issues and plans. In addition, casual conversations are always thought to be more secure, and an electronic beacon controlled by Flame provides one of the most difficult capabilities to acquire in the intelligence business – a mole.
More specifically, recorded voice conversations can lead to voice print analysis for the purpose of identifying key personalities, their roles and their vulnerability to things like blackmail, kidnap or worse. Voice print biometric analysis today can provide fingerprint-level accuracy.
Final analysis
Flame has been rightly described as the most sophisticated cyber weapon ever discovered. But its intelligence gathering mission has been undervalued and misrepresented.
It is clear from the design and intentions of the controllers that Flame is the work of a state-sponsored intelligence community, most likely that of the United States or Israel. And while there have been valid concerns raised about the threat of blowback (inadvertent infections of your own critical infrastructure and the ability of adversaries to reverse-engineer the code into something more capable), most of the firms in the anti-virus industry have now caught up to the latest version of Flame (the latest of a dozen different variants).
Even Microsoft Corp. has issued three critical updates in the aftermath of Flame. The malware was successful in redirecting clients that were seeking to download standard Windows Updates to an infected machine. Flame leveraged a fake Microsoft certificate to send a fake update to the requesting machine. That machine would then download what it thought was a valid Microsoft update, but in reality it was downloading a full version of Flame.
Some may want to call this a cyber war. But for me and others who look at this through a different set of professional goggles, Flame appears to be a significant attempt by the United States to understand exactly where the Iranian nuclear program is, where it is going in its development and how rapidly. At worst, Flame is a drastic attempt to collect critical missing data that may mean the difference between success and failure during a military strike targeting Iranian nuclear facilities.
So far, Flame has not provided us any other raison d’être.
Dan Verton is director of Homeland Security Today’s Multimedia Division. A former intelligence officer, he's an award-winning technology journalist and author of the acclaimed book, Black Ice: The Invisible Threat of Cyber-Terrorism.
Artwork courtesy of Kaspersky Lab
Read more:
http://www.hstoday.us/briefings/today-s-news-analysis/single-article/deciphering-flame-an-intelligence-officer-s-perspective/7c912c695d278f42b8194a4b0e7590a5.html
