Jul 1, 2012 4:45 AM
EDT
Espionage is physically and mentally unforgiving, and anything but exotic. A psychologist to the clandestine world on the unseen toll—and true heroes—of intelligence work.
Every few years, major news breaks about spying, with stories of spectacular heroism and shocking betrayal. What goes on in the mind of those who inhabit the clandestine world?
In early May, the world learned of a real example of heroic espionage.
Intelligence officials foiled an al Qaeda plot to bring down a plane by having a suicide operative smuggle on board a nonmetallic exploding device concealed beneath his clothing. The terrorist group failed because the operative they chose for the mission was widely reported to have been
an agent of British or Saudi intelligence. For those of us in the business, it was rare to see an agent’s heroism come to light, though we get to witness their bravery covertly on a routine basis in our daily work. What do people outside the clandestine world not see?
Many Spies Are Not Heroic
Intelligence officers who handle espionage sources—variously called informants, assets, or agents, to distinguish them from the professionals—and the psychologists they consult with study the motives of agents closely. These motivations are often self-serving. Some want money, or the excitement of a
James Bond adventure, or to believe they are playing dramatic, if hidden, roles in historical events.
Some are aggrieved and seek revenge. Some agents spy as a kind of sport. They like sneaking around and manipulating others, and feel superior to their oblivious targets drawn into hidden games of secrecy and deception.
In Some Places, Only Heroes Will Spy
Heroic spies are an entirely different type of human being, set apart from ordinary clandestine players not by the tradecraft they use—which is universal—but by their fundamental values. Their motives are not self-serving—the risks of espionage in the contexts they serve in are too high to draw in selfish people. They are morally revolted by their targets’ conduct and dismayed at the future they’re intent on building or have already actualized.
It is nearly impossible for intelligence professionals to keep agents safe when they are spying against groups such as the current terrorist targets—as was also the case with
Soviet Russia or
Saddam Hussein’s Iraq. Most sane prospective spies realistically assessing the ruthlessness and counterintelligence capabilities of targets like al Qaeda choose to stand down from entering espionage. Heroic agents are the small group of sane people who make the same assessments, but make a different choice.

Corbis
The Losses and Stress Can Be Punishing
A case-officer colleague of mine, formerly a member of an elite military combat unit, was handling a source who was captured and then killed in the village square in front of friends and relatives by terrorists using the drawn-out methods worthy of medieval torturers. As we discussed the nature of his lost agent, my colleague remarked that the world had lost that day an unrecognized prince, a noble and civilized man whose war flag—if the work of spies permitted such emblems of service—should have been flown high at his funeral and included symbols of both an eagle and a dove.
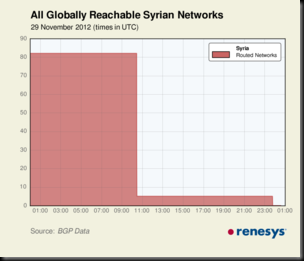 Looking closely at the continuing Internet blackout in Syria, we can see that traceroutes into Syria are failing, exactly as one would expect for a major outage. The primary autonomous system for Syria is the Syrian Telecommunications Establishment; all of their customer networks are currently unreachable.
Looking closely at the continuing Internet blackout in Syria, we can see that traceroutes into Syria are failing, exactly as one would expect for a major outage. The primary autonomous system for Syria is the Syrian Telecommunications Establishment; all of their customer networks are currently unreachable.