Click for latest update: 01:00 GMT Friday.
Starting at 10:26 UTC on Thursday, 29 November (12:26pm in Damascus), Syria's international Internet connectivity shut down. In the global routing table, all 84 of Syria's IP address blocks have become unreachable, effectively removing the country from the Internet.
We are investigating the dynamics of the outage and will post updates as they become available.
Update (15:45 UTC) 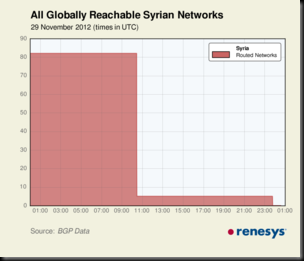 Looking closely at the continuing Internet blackout in Syria, we can see that traceroutes into Syria are failing, exactly as one would expect for a major outage. The primary autonomous system for Syria is the Syrian Telecommunications Establishment; all of their customer networks are currently unreachable. Looking closely at the continuing Internet blackout in Syria, we can see that traceroutes into Syria are failing, exactly as one would expect for a major outage. The primary autonomous system for Syria is the Syrian Telecommunications Establishment; all of their customer networks are currently unreachable. Now, there are a few Syrian networks that are still connected to the Internet, still reachable by traceroutes, and indeed still hosting Syrian content. These are five networks that use Syrian-registered IP space, but the originator of the routes is actually Tata Communications. These are potentially offshore, rather than domestic, and perhaps not subject to whatever killswitch was thrown today within Syria. |

